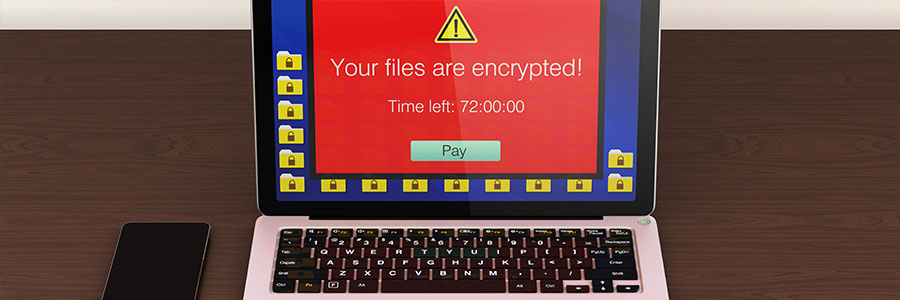
We’ve gotten so caught up discussing ransomware prevention with our clients that we’ve neglected to mention that several strains have already been defeated. In fact, there’s a decent chance you can actually decrypt all your data for free. Make sure to check these free resources before responding to a cyberattacker’s demands.
Check the list of free ransomware decryptors